Originally published on Techwire: Zero Trust Security Model with Microsoft 365
Today, organizations need a new security model that effectively adapts to the complexity of the modern environment, embraces the mobile workforce, and protects people, devices, applications, and data wherever they are located.
While Zero Trust concepts have been around for more than a decade, many organizations are still working to ensure a full understanding of the model within their security and operational teams. Microsoft’s Zero Trust definition is:
Instead of assuming everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originates from an open network. Regardless of where the request originates or what resource it accesses, Zero Trust teaches us to “never trust, always verify.” Every access request is fully authenticated, authorized, and encrypted before granting access. Micro-segmentation and least privileged access principles are applied to minimize lateral movement. Rich intelligence and analytics are utilized to detect and respond to anomalies in real time.
A Zero Trust approach should extend throughout the entire digital estate and serve as an integrated security philosophy and end-to-end strategy. This is done by implementing Zero Trust controls and technologies across six foundational elements. Each of these is a source of signal, a control plane for enforcement, and a critical resource to be defended:
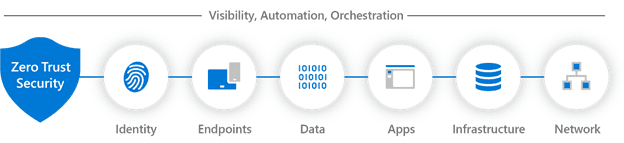
- Identities: Verify and secure every identity with strong authentication across your entire digital estate.
- Endpoints: Gain visibility into devices accessing the network and ensure compliance and health status before granting access.
- Data: Classify, label, and protect data across cloud and on-premises to thwart inappropriate sharing and insider risks.
- Apps: Discover Shadow IT and control access with real-time analytics and monitoring.
- Infrastructure: Harden defenses using granular access control, least privilege access principles, and real-time threat detection.
- Network: Move beyond traditional network security with micro-segmentation, real-time threat detection, and end-to-end encryption.
Planet Technologies offers Microsoft 365 G5 Security Assessment and Roadmap engagements to help your organization plan for successful Zero Trust implementations that focus on business outcomes, budget allocations, and internal alignment that engages directly with users to make security a driving force to improve their experiences and productivity.
For more information on starting your Zero Trust journey contact Jennifer Dodd at jdodd@go-planet.com

