Originally published on Techwire: 6 Ways to Secure Your M365 Tenant in the New Year
Every New Year many people set resolutions to change their diet, go to the gym more, or cook more at home. The same goes for organizations and governments. The State of California has multiple initiatives in 2022 to increase their ability to ensure information security. Make this the year your organization improves its security posture with these 6 foundational Microsoft 365 (M365) best practices.
Baseline Conditional Access
Conditional Access provides the ability to make intelligent access decisions based on several signals such as user location, role, AD group, and risk. Blocking access based on risky locations or device risk can prevent attackers from being at the forefront.
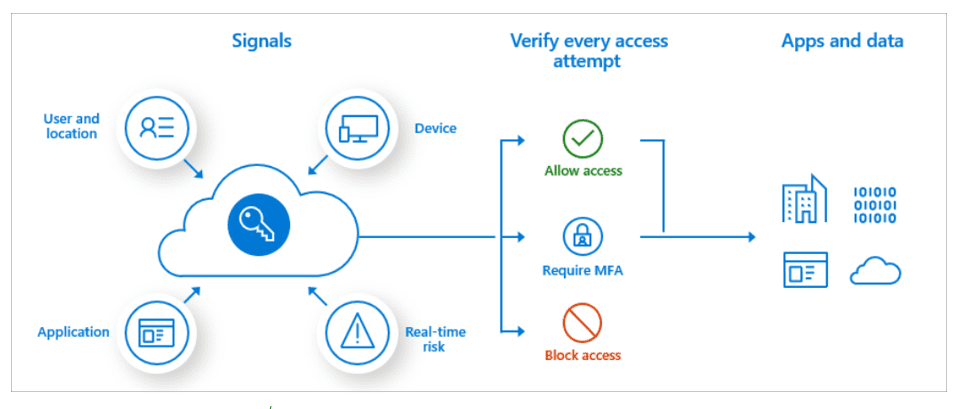
Figure 1: Conditional Access flow
Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is a process where a user must provide an additional form of identification during a typical sign-in process. These forms of identification could be something you know, like a password; something you have, like a device, phone, or hardware key; or something you are, like a fingerprint or face scan. Implementing MFA within the organization drastically secures your identities
Cloud Application Consent
Shadow IT is a concept that refers to technology or cloud services outside of the IT department’s control. A common form this takes is with users’ ability to consent to their data being used in cloud services. This is particularly true with Azure AD’s easy integration as the authentication mechanism for 3rd party cloud apps where users can consent to allow applications to access their data such as read access to an outlook calendar or basic identification information stored in Azure AD. Preventing user consent to risky 3rd party apps cuts down on our exposure to Shadow IT risk.
Baseline Data Loss Protection
Data Loss Prevention (DLP) is technology that protects sensitive data from exfiltration. This sensitive data may be things like Social Security Numbers, Driver’s License Numbers, or Banking Account information. DLP is controlled through policies that are managed by Microsoft Information Protection (MIP) and should be implemented to get control over potential exfiltration.
Privileged Identity Management
Azure AD Privileged Identity Management (PIM) focuses on protecting admin accounts and ensuring concepts like just-in-time access or least privileged access. Azure AD PIM allows for the ability to enforce these concepts on highly privileged AAD accounts and should be enforced across the tenant.
Azure AD Identity Protection
Risk is a term often used when talking about security, and in Azure AD terms represents the probability that a given authentication request is not authorized by the identity owner. Azure AD Identity Protection allows us to assess sign-in risk and user risk. AAD Identity Protection looks at several factors such as anonymous IP address used, atypical travel, malware linked IP address, sign-in from leaked credentials, and various other unfamiliar sign-in properties. This risk should be used as a means for access to resources managed by Azure AD.
Are you looking for help improving your security in M365? Contact Jen Dodd at [email protected] for more information!
About Planet Technologies
Founded in 1998, Planet Technologies is the leading provider of Microsoft 365 and hybrid cloud consulting services to the public sector. Planet supports all areas of the federal government, state and local agencies, and educational institutions across the country. We are in the business of trust and most of our clients are repeat customers – our greatest achievement. Planet has been awarded Microsoft Cloud Partner of the Year, Microsoft Security Partner of the Year, Microsoft Federal Partner of the Year, Microsoft State and Local Government Partner of the Year, and Microsoft Windows Partner of the Year.

