Not so long ago, identities were a matter of defining an access perimeter and giving access to the people you knew needed access.
This has changed a lot and companies and organizations cannot just manage a perimeter anymore. The world has changed and what used to be a directory (or two) is now many services out there somewhere that we need to know a whole lot more about the user to manage access and governance.
To manage identities, we no longer focus only on a directory and access, it is now much more than network access. It is about securing access to and from everything:
Verify Explicitly and Trust Nothing
Also, what used to only be about securing human access now we must include services, networks, devices, apps, and databases. Identity scopes have moved beyond our local network; access must be granted and consumable automatically and in real time across SaaS solutions, AWS, Google Cloud, Azure AD, Active directory, web sites and apps, everywhere. Without SSO to all apps, the offboarding process has also become unmanageable.
Enter Microsoft Entra
Microsoft Entra is a new product family that encompasses all of Microsoft’s identity and access capabilities. The Entra family includes Microsoft Azure Active Directory (Azure AD), as well as two new product categories: Cloud Infrastructure Entitlement Management (CIEM) and decentralized identity.
Microsoft Entra is made up of three building blocks:
- Azure Active Directory
- Permission Management
- Verified ID
So Why is Entra Such a Big Deal?
For starters we need to think about how an organization on boards and offboards. How an Agency onboards needs to be quick and accurate. In my experience I have seen organizations take more than a week to give out the permissions needed to a new employee. That slow down causes the employee frustration and hurts their efficiency and how soon they can be a productive member of a team. For offboarding the problem is even worse. There are huge security risks at play in that if your organization has not integrated SSO to every app and SaaS then you risk that employee having access to corporate tools after their employment. Think drop box or someone who maintains a twitter account for the company, and this becomes clear quickly how big of a deal this is. If those 2 issues weren’t big enough, now think about how many people must be contacted to set up permissions for Business to Business to work with external partners. Entra can solve all of this and more.
Consider Microsoft Entra as an alternative to SSO – we all know the backend plumbing that goes into making SSO work across services, devices, regions, and user identities.
How Does Verifiable Credentials Work?
Verifiable Credentials allow for the digital proofing of claims data through a combination of public key cryptography and privacy-preserving techniques to prevent correlation. The effect of this is that now, not only can physical credentials safely be turned into digital tokens or credentials. The owner of such credentials can selectively share specific information from this credential without exposing the actual data (for example verifying age without having to show your physical ID card), where third parties are instantly able to verify this data without having to call upon the issuer. This contrasts with existing digital wallets, such as Apple Pay that requires data management and agreements (think federation setup) before the solution accepts transforming the object as a digital token.

Microsoft Entra – Getting Started
Microsoft Entra is in public preview and offers administrators to access the new Microsoft Entra admin center.
Microsoft Entra is enabled automatically on your Azure AD tenant and is accessed via https://entra.microsoft.com/ to give you more focused identity governance in the admin portal. Your login is passed on from your Azure Portal or can be accessed directly using your tenant credentials.

Microsoft Entra Admin Center
Access and administer the Microsoft Entra family of products through the admin center
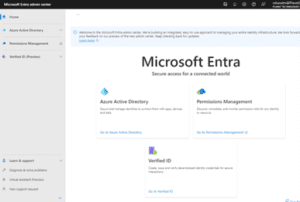

Azure Active Directory
Microsoft Azure Active Directory (Azure AD), part of Microsoft Entra, provides an identity and access management solution with integrated security to manage and protect all your users and data.

Active directory delivers Identity protection and security services and also is enabled with Azure Active Directory Verified Credentials Service to support the model of Decentralized Identities.
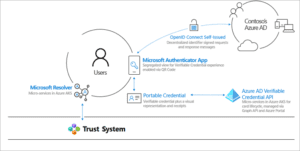
- W3C Decentralized Identifiers (DIDs): IDs users create, own, and control independently of any organization or government. DIDs are globally unique identifiers linked to Decentralized Public Key Infrastructure (DPKI) metadata composed of JSON documents that contain public key material, authentication descriptors, and service endpoints.
- Trust System: To be able to resolve DID documents, DIDs are typically recorded on an underlying network of some kind that represents a trust system. Microsoft currently supports two trust systems, which are:
- DID User Agent/Wallet: Microsoft Authenticator App. Enables real people to use decentralized identities and Verifiable Credentials. Authenticator creates DIDs, facilitates issuance and presentation requests for verifiable credentials and manages the backup of your DID’s seed through an encrypted wallet file.
- Microsoft Resolver: An API that connects to our ION node to look up and resolve DIDs using the did:ion method and return the DID Document Object (DDO). The DDO includes DPKI metadata associated with the DID such as public keys and service endpoints.
- Azure Active Directory Verified Credentials Service: An issuance and verification service in Azure and a REST API for W3C Verifiable Credentials . They enable identity owners to generate, present, and verify claims. This forms the basis of trust between users of the systems.

Microsoft Entra Permissions Management
One unified model to manage permissions of any identity across any cloud: Microsoft Entra Permissions Management is a cloud infrastructure entitlement management (CIEM) product that provides comprehensive visibility and control over permissions for any identity and any resource in Microsoft Azure, Amazon Web Services (AWS) and Google Cloud Platform (GCP). It also streamlines getting new employees and external employees the permissions they need without having to know all the individuals needed to gain access by assigning access packages to applications, groups, Teams, and SharePoint sites, with multi-stage approval, and ensures users don’t retain access indefinitely through time-limited assignments and recurring access reviews.
The Entra CIEM solution is not to be confused with the Azure AD Entitlement Management
Source: Microsoft
For example, over-privileged workload and user identities, actions, and resources across multi-cloud infrastructures in Microsoft Azure, Amazon Web Services (AWS), and Google Cloud Platform (GCP). Permissions Management detects, automatically right-sizes, and continuously monitors unused and excessive permissions.

Microsoft Entra Verified ID
Key scenarios
During the Entra preview period, customers from around the world have issued and verified credentials across a variety of scenarios, ranging from remote onboarding at work, and collaboration across business boundaries to enabling education beyond the campus. Customers have issued and verified tens of thousands of credentials using our platform across a diverse set of industries to enable:
- Faster remote onboarding: Validate identity information for trustworthy self-service enrollment and reduced time-to-hire.
- Verify access to high value apps: Quickly verify an individual’s credentials and status to grant least-privilege access with confidence.
- Easy account recovery: Replace support calls and security questions with a streamlined self-service process to verify identities.
The API first approach makes it easy for customers to integrate verifiable credentials in their existing apps and enables an easy jumpstart model to improve verifiability and compliance. These apps and services could be hosted on-premises or on Azure, AWS or GCP.
Microsoft Entra Verified ID is included with any Azure Active Directory subscription, including Azure AD Free
Customers rely on Azure AD to secure access to corporate resources. However, enabling use of credentials for utility beyond the company, such as verifying employment for a loan, is complex and can have compliance risk.
- Issue credentials: Customers can now design and issue verifiable credentials to represent proof of employment, education, or other claims. A holder of a credential can decide when, and with whom, to share it. Each credential is signed with cryptographic keys that the user owns and controls. These credentials can be presented and validated even if the issuing institution no longer exists.
- Request and verify credentials: Unlike credentials issued by current centralized identity systems, verifiable credentials are standards-based. This makes it easy for developers to understand and does not require custom integrations. Applications can request and verify the authenticity of credentials from any organization using APIs included as part of the service.
- Present credentials in a privacy respecting, secure manner: Users can manage and present credentials using Microsoft Authenticator. What makes this unique is it enables users to control who can access them, even if credentials are issued by organizations. We will be adding capabilities like selective disclosure, derived claims (e.g. proof of age instead of birth date) and measures preventing correlation.
- Recover credentials: End-users can manage credentials using Microsoft Authenticator and recover from loss using a mnemonic-based (pass phrase) scheme. We continue to partner with the community to find more user friendly, elegant means of enabling recovery. In addition, we will provide custodial and social recovery solutions so users can choose a circle of trusted parties, across friends, family, and organizations.
Learn more about verifiable credentials and decentralized identity:
- Secure Access for a connect world https://www.microsoft.com/security/blog/2022/05/31/secure-access-for-a-connected-worldmeet-microsoft-entra/
- Streamlining employee onboarding: Microsoft’s response to the Great Reshuffle
- Get customer stories and verifiable credentials resources at http://aka.ms/verifyonce
- Understand the basics of decentralized identity via our five-part blog series
- Quick overview: http://aka.ms/didexplained
- Documentation for developers: http://aka.ms/didfordevs
- Get involved with http://identity.foundation, industry working group for all things Decentralized ID (DID)
- How to deploy Azure AD entitlement management in your organization
- How to monitor and scale your use of Azure AD entitlement management
- How to delegate in entitlement management
Next Steps
- If you’re interested in using the Azure portal to manage access to resources, see Tutorial: Manage access to resources – Azure portal.
- if you’re interested in using Microsoft Graph to manage access to resources, see Tutorial: manage access to resources – Microsoft Graph
- Common scenarios

