Operationalizing Zero Trust security posture involves implementing a comprehensive security framework that verifies and secures every access request, regardless of the user’s location or device. But keep in mind, implementing Zero Trust is not a one-time project but an ongoing journey. Regularly review and update your security policies, access controls, and configurations based on the evolving threat landscape and your organization’s needs.
Zero Trust is a security posture that is built on three core principles to be successful:
- Verify explicitly – Always authenticate and authorize based on all available data points.
- Use least privilege access – Limit user access with risk-based adaptive policies, and data protection.
- Assume breach – segment access and minimize impact in the event of a breach.
Assuming a zero-trust mindset represents shift from a traditional security posture. In today’s cloud centric world, we can no longer assume securing network perimeter will secure the organization. In this Cloud first world, we must take a holistic security approach that begins with the identity and extends to the data layer and successfully encompasses all aspects of the foundational elements of zero trust with dynamic policies. This becomes critical for any organization seeking to effectively protect their environments and demonstrate our compliance with compliance NIST 800-171 and CMMC 2.0. We often find that beginning the zero-trust journey can effectively help us accomplish both goals in a singular path.
A Zero Trust journey should extend throughout the entire digital estate of an organization and serve as an integrated security philosophy and end-to-end strategy. This is done by implementing Zero Trust controls and technologies across six foundational elements. Those elements include:
- Identity
- Endpoints
- Data
- Apps
- Infrastructure
- Network
Now that we understand the pillars and the foundational elements the next steps are where do we begin the journey. One way we can do that is ask ourselves the following questions and assess where we are on our zero-trust journey and where do we go from here.
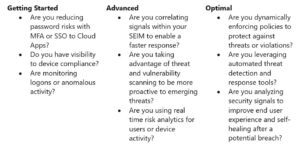
So, what is the next step? Zero Trust is a dynamic process. Different organizational requirements, existing technology implementations, security stages and compliance requirements can all impact an organization’s journey to Zero Trust. During our next YouAlreadyOwnIt Cloud Office Hours we will share our experience in helping customers to secure their organizations, as well as in implementing our own Zero Trust model and look at different trends that we can look at to help accelerate our journey. In addition, we will show how this model can help expedite an organization’s path to demonstrate compliance with NIST 800-171 or CMMC 2.0. We plan to share guidance to assess your readiness and to help you build a plan to get to Zero Trust.

